 Continuous Scanning
Continuous Scanning
Automatic and continuous scanning of pages to detect potential security threats.


 Continuous Scanning
Continuous Scanning
Automatic and continuous scanning of pages to detect potential security threats.
 Expert Analysis
Expert Analysis
Each detected threat is carefully analyzed by our specialists to ensure precision and reliability of reports.
 Convenient User Panel
Convenient User Panel
All information about detected vulnerabilities is presented transparently in our panel, along with their classification according to importance.
NightWatchDog provides advanced cybersecurity monitoring for your websites, offering crucial insights and protection against vulnerabilities. Key benefits include:
Detailed Infrastructure Scanning: We thoroughly scan your infrastructure, identifying all ports, hosts, web applications, and files, presenting this information clearly for easy analysis.
Comprehensive Security Scanning: We detect vulnerabilities across web applications, network services, and IT infrastructure. Each detection is verified by expert analysis to eliminate false positives, providing you with confirmed vulnerabilities.
Real-time Vulnerability Insights: Get immediate, actionable insights on detected vulnerabilities, categorized by severity to help prioritize your security efforts efficiently.
Interactive Dashboard: Our dashboard presents issues that need attention and includes a geomap marking all your hosts, with information on whether a host is infected.
24/7 Monitoring: Continuous surveillance to detect and respond to threats at any time.
User-Friendly Interface: Easy-to-navigate platform for managing and understanding security status.


On average, it takes 204 days to identify a data breach. Can you afford the wait?
Contain a data breach in 73 days? Speed up with our tools!
In 2023, data breaches cost an average of $4.45 million globally. Protect your assets!
U.S. businesses face an average breach cost of $5.09 million. Don’t be a statistic.
Remote work data breaches cost an extra $173,074. Secure your remote workforce.
75% of companies suffer material disruption from breaches. Be in the safe 25%.
Lost business accounts for 37.5% of breach costs. Prevent loss with our solution.
72.7% of organizations hit by ransomware in 2023. Strengthen your defenses.
Recovering from ransomware (excluding ransom) costs $1.82 million. Mitigate risks now!
Only 8% of ransom-paying businesses recover all data. Invest in prevention.
Hackers attack every 39 seconds. Stay vigilant with real-time monitoring.
Organizations face 26,000 cyberattacks daily. Are you prepared?
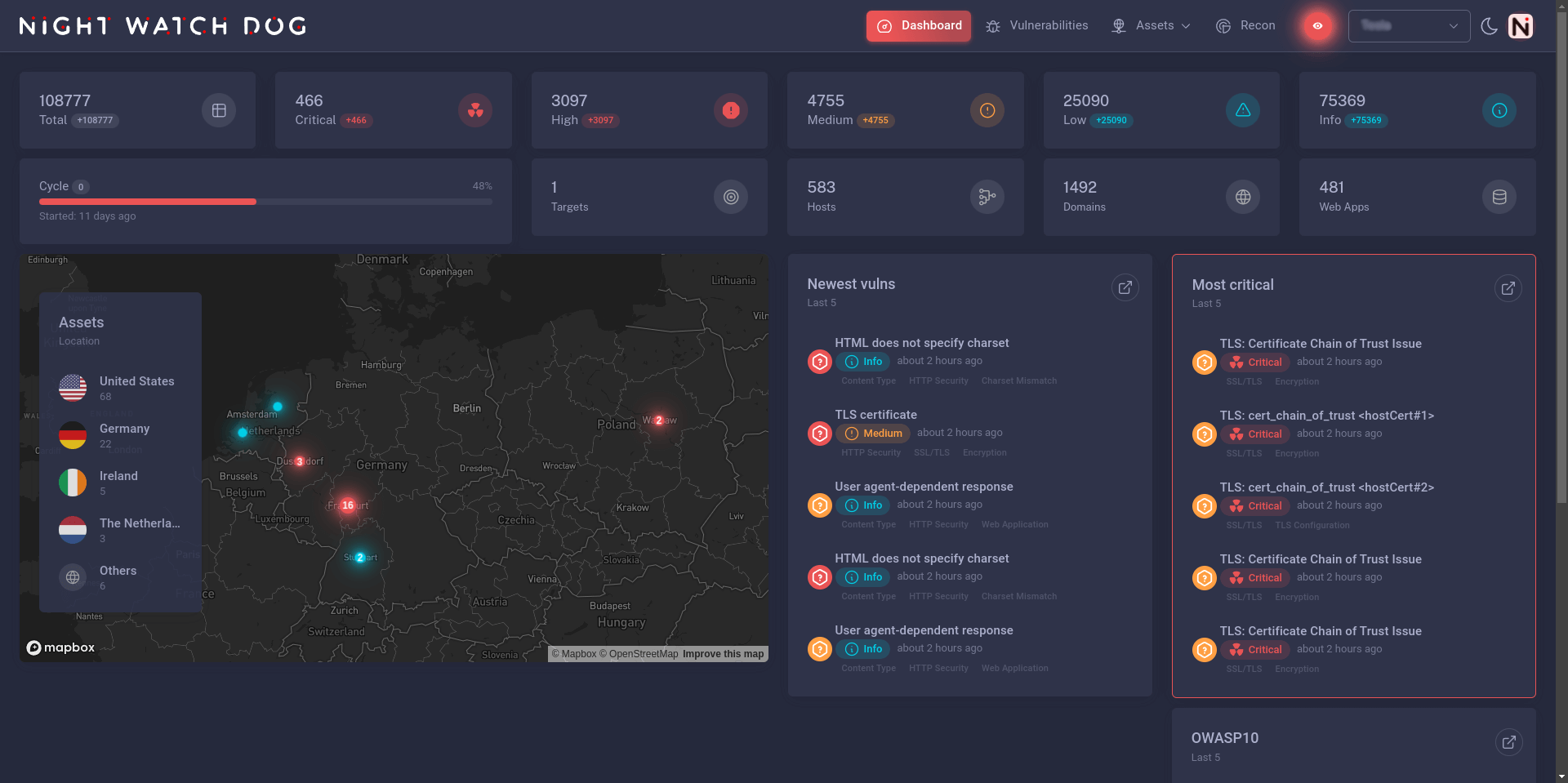
Many victims never even realise they were hacked. Request offerOur dashboard is designed to provide you with a real-time, comprehensive view of your security landscape, enabling you to make informed decisions and prioritize actions efficiently.
Gain a clear summary of your assets' counts, offering a quick overview of the scale and distribution of your digital resources, enhancing your understanding of the potential attack surface.
Highlight the most critical vulnerabilities within your network, ensuring that the most severe risks are addressed promptly to minimize potential impact.
Gain complete visibility of your external assets with our geomap feature. Spot potential attacker entry points and get alerts about new external-facing exposures. This global view enables you to understand the geographical distribution of your assets, making it easier to identify and mitigate risks associated with specific locations.
Our Vulnerabilities page is engineered to offer a detailed, actionable, and up-to-date view of the security vulnerabilities within your digital infrastructure. With a focus on accuracy and depth, this feature empowers you to bolster your defenses without the noise of false positives.
Our advanced scanner tirelessly checks your pages against the latest vulnerabilities, ensuring that your defenses are always a step ahead. This continuous monitoring means that as soon as a new threat emerges, we're on it, providing you with the most current protection.
Quickly understand the risk landscape with vulnerabilities categorized by severity levels—Critical, High, Medium, Low, Info. This clear segmentation allows you to prioritize remediation efforts where they are needed most, ensuring efficient allocation of resources.
Not only do we identify vulnerabilities, but we also provide detailed information on how each was detected and step-by-step guidance on how to fix them. These insights are presented in a modern, user-friendly design, making it easier for you to understand and act on the information provided.
The Attack Surface page is meticulously crafted to give you a panoramic yet detailed view of your entire digital landscape. By identifying and mapping out all your digital assets, we empower you with the knowledge to secure your perimeter effectively.
Dive deep into your digital domain with our extensive scanning capabilities. We meticulously search for domains, web applications, hosts, and ports, leaving no stone unturned. This thorough examination ensures that every part of your digital presence is accounted for and assessed for vulnerabilities.
Gain valuable insights with information on the location of your hosts, presented through an interactive geomap. This feature not only enhances visibility over your assets but also helps in identifying patterns or risks associated with specific geographical locations.
With our intuitive asset tree, visualize the relationship between your assets (from domains to web apps and hosts to ports). This structured visualization aids in understanding how your assets interconnect, highlighting potential vulnerabilities in the architecture and facilitating targeted security measures.
leave us your details and we will contact you with an offer.

